SpamPal
is very configurable but the
default settings should suit most user's needs. If however,
you need to change the default settings, you can tune SpamPal using
the Options
panel.
|
1.
Access the Options Panel
2. Connections
2.1. Connections: Main
Pane
2.2. Connections: Port Properties: POP3 Proxy
Setup (any username)
2.3. Connections:
Port Properties: POP3 Proxy Setup (specific servername)
2.4. Connections:
Port Properties: IMAP4 Proxy Setup (any username)
2.5. Connections:
Port Properties: IMAP4 Proxy Setup (specific servername)
2.6. Connections:
Port Properties: SMTP Proxy Setup (auto whitelisting)
3 Spam-Detection
3.1. Spam-Detection: Whitelist:
Email Addresses
3.2. Spam-Detection: Whitelist: Automatic
3.3. Spam-Detection: Whitelist: Automatic: Exclusions
3.4. Spam-Detection: Blacklists: Public blacklists
(DNSBLs)
3.5. Spam-Detection: Blacklists: Countries
3.6. Spam-Detection: Blacklists: Email-Addresses
3.7 Spam-Detection: Blacklists: I.P. Addresses
3.8. Spam-Detection: Ignore-Lists: Providers
3.9. Spam-Detection: Ignore-Lists: I.P. Addresses
3.10. Spam-Detection: Ignore-Lists: Automatic
4. Message-Tagging
5. Interface
6. Logging
7. Updates
8. Advanced
8.1. Advanced: Lan Configuration
8.2. Advanced: Access Control
8.3. Advanced: Extra Black/White/Ignore Lists
8.4. Advanced: Extra DNSBL Definitions 9. Plugins
10. Command Line options
10.1 Command
Line options: Configuration Directories
10.2 Command
Line options: Multiple Instances
10.3 Command
Line options: Tray Icon
|
::Top:: |
| To
access the Options panel, Right-click
on SpamPal's umbrella tray icon, then click on Options. |
|
|
::Top:: |
|
This pane allows you
to control the port(s) your email
program uses to communicate with SpamPal. You can normally leave
these port numbers, on the values set by SpamPal and not worry about
it too much.
The default
enabled Ports are 110
(POP3), 143 (IMAP4). You may also
see Port 25 (SMTP).
|
|
|
::Top:: |
In most
cases, you will be using SpamPal's POP3 Proxy, when setting up SpamPal.
From the main Connections
screen (see above), click Add
to create a new port (or select Properties
to
modify the settings)
In the Setting tab screen
below, which is currently set to a port type of POP3
(any servername) you can see that the
only setting you may wish to modify is the Local
Port Number. The main reason for wanting
to change from the default pop3 port
of 110,
is if there is a conflict with
another program, such as an anti-virus scanner (see this page
for more details on how to find conflicts): |
|
|
| In the Options
Tab screen below, you will find various options to change the
way the pop3 connection operates: |
|
Suppress Connection
error messages in Client; If your
email program is set to check for mail automatically, after installing
SpamPal, it may give you errors
after you go offline. If you enable this option, you can suppress
the error messages.
Don't report networking error
messages; If you enable this
option, you can suppress any error messages from SpamPal
it may give you, for example, if your system goes offline
or your Internet Provider's server has a problem.
Attempt APOP authenification; If
your Internet Provider requires you to use APOP (Authenticated POP),
a more secure method of sending your password to the server,
then select this
option in SpamPal and deselect any corresponding APOP option
within your email
program.
|
For message previews; There
isn't much point filtering the entirity of large messages, when
you email program is only asking to look the headers of you email.
This allows you to specify how much of the message body should
be filtered by a plugin like RegExFilter or HtmlModify. Lower
values will make SpamPal operate quicker, but at the expense
of slightly less accuracy.
For full message; There
isn't much point filtering the entirity of large messages, so
this allows you to specify how much of the message body should
be filtered by a plugin like RegExFilter or HtmlModify. Lower
values will make SpamPal operate quicker, but at the expense
of slightly less accuracy. |
| |
|
| |
::Top:: |
If you need to
use Secure Password Authentication,
SASL or APOP
authentication, you cannot
use the POP3 (any username) option, Instead, you have to use the POP3 (specific servername) option.
Ie. you
have to tell SpamPal directly what pop3 server is
it to use.
From
the main Connections
screen, click Add
to create a new port (or select Properties
to modify the settings).
|
|
|
In the Setting
tab screen above, which is currently
set to a port type of POP3 (specific
servername) you can modify is the Local
Port Number. The main reason for
wanting to change from the default pop3 port
of 110,
is if there is a conflict
with another program, such as an anti-virus scanner (see this page
for more details on how to find conflicts).
In this method of specifying server names, every server must
have a different port number. The default port
number for POP3 is 110,
but obviously only one server will be able to use this,
so if you have more than one mailserver give them different port numbers.
Almost any
number about 1024 and about 10000 should be okay.
On this screen, you also enter
the POP3
server name (usually
of your ISP) that you are going to use. |
|
|
Suppress Connection
error messages in Client; If your
email program is set to check for mail automatically, after installing
SpamPal, it may give you errors after you go offline. If you
enable this option, you can suppress the error messages.
Don't report networking error
messages; If you enable this
option, you can suppress any error messages from SpamPal
it may give you, for example, if your system goes offline
or your Internet Provider's server has a problem.
Attempt APOP authenification; If
your Internet Provider requires you to use APOP (Authenticated
POP), a more secure method of sending your password
to the server, then select
this option in SpamPal and deselect any corresponding
APOP option within your email program.
|
For message previews; There
isn't much point filtering the entirity of large messages, when
you email
program is only asking to look the headers of you email. This
allows you to specify how much of the message body should be
filtered by a plugin like RegExFilter or HtmlModify. Lower
values will make SpamPal operate quicker, but at the expense
of slightly less accuracy.
For full message; There
isn't much point filtering the entirity of large messages,
so this allows you to specify how much of the message body
should be filtered by a plugin like RegExFilter or HtmlModify. Lower
values will make SpamPal operate quicker, but at the expense
of slightly less accuracy.
|
| The
defaults for Message
Preview is 4K and the Full
Message: 64K
Try setting both values to the same thing, e.g. 64K, and see
if that cures the problem. |
|
|
|
| |
::Top:: |
| From
the main Connections
screen, click Add
to create a new port (or select Properties
to modify the settings) |
|
|
|
|
Don't report networking
error messages; If you enable this
option, you can suppress any error messages from SpamPal it may
give you, for example, if your system goes offline or your Internet
Provider's server has a problem.
Add X-SpamPal Header -
allowing SpamPal to modify the message headers (or body) is very
slow in IMAP4, as the entire message has to be downloaded
by SpamPal, modified, then uploaded back to your mailserver. Therefore,
by default SpamPal allows no changes to the headers or body of
the message - no **SPAM** tags in the subjects, no X-SpamPal: header
lines, etc. You can make SpamPal add these to all or just
spam messages by using this option.
Automatically delete
spam messages - will mark as deleted any messages that
SpamPal detects to be suspected spam. By default, this is disabled,
and I strongly recommend that
it remains disabled until you are very confident that
this won't result in anything important getting mistakenly deleted,
or possibly forever.
Automatically move
spam messages - SpamPal's default action for an IMAP4
account is to move spam messages to another folder. You can specify
the folder name here - if it doesn't exist then SpamPal will
try to create it, and give you an error message if it fails.
Filter first xx k
of message body - There isn't much point filtering the
entirity of large messages - this allows you to specify how much
of the message body should be filtered by a plugin like RegExFilter or HtmlModify. Lower
values will make SpamPal operate quicker, but at the expense
of slightly less accuracy
|
|
| Filter Messages: with Recent
flag / without Seen flag / all - this
is a technical setting that you probably won't need to alter from
with Recent flag. A
few IMAP4 servers out there seem not to set the Recent flag
correctly, however, so if SpamPal seems to not filtering some or
all of your mail, try altering this to without
Seen flag, and if it still
doesn't work set it to all. |
|
| |
::Top:: |
If you need to
use Secure Password Authentication or SASL authentication, you
cannot use the IMAP (any username) option,
Instead, you have to use
the IMAP (specific servername) option.
Ie. you have to tell SpamPal directly what IMAP
server is it to use.From
the main Connections
screen, click Add
to create a new port (or select Properties
to modify the settings) |
|
|
In the Setting
tab screen above, which is currently
set to a port type of IMAP4 (specific
servername) you can modify is the Local
Port Number. The main reason for
wanting to change from the default IMAP4 port
of 143,
is if there is a conflict
with another program, such as an anti-virus scanner (see this page
for more details on how to find conflicts).
In this method of specifying server names, every
server must have a different port number. The default
port number for IMAP4 is 143,
but obviously only one server will be able
to use this, so if you have more than one mailserver
give them different port numbers. Almost any
number about 1024 and about 10000 should be okay.
On this screen, you also enter the IMAP4
server name (usually of your ISP) that
you are going to use. |
|
|
Don't report networking
error messages; If you enable this
option, you can suppress any error messages from SpamPal it may
give you, for example, if your system goes offline or your Internet
Provider's server has a problem.
Add
X-SpamPal Header -
allowing SpamPal to modify the message headers (or body) is very
slow in IMAP4, as the entire message has to be downloaded
by SpamPal, modified, then uploaded back to your mailserver. Therefore,
by default SpamPal allows no changes to the headers or body of
the
message - no **SPAM** tags in the subjects, no X-SpamPal: header
lines, etc. You can make SpamPal add these to all
or just spam messages by using this option.
Automatically delete
spam messages - will mark as deleted any messages that
SpamPal detects to be suspected spam. By default, this is disabled,
and I strongly recommend that
it remains disabled until you are
very confident that this won't result in anything important getting
mistakenly deleted, or possibly forever.
Automatically move
spam messages - SpamPal's default action for an IMAP4
account is to move spam messages to another folder. You can specify
the folder name here - if it doesn't exist then SpamPal will
try to create it, and give you an error message if it fails.
Filter first xx k
of message body - There isn't much point filtering the
entirity of large messages - this allows you to specify how much
of the message body should be filtered by a plugin like RegExFilter or HtmlModify. Lower values will make SpamPal operate quicker,
but at the expense of slightly less accuracy
|
|
|
| Filter Messages: with Recent
flag / without Seen flag / all - this is a technical setting
that you probably won't need to alter from with Recent flag. A
few IMAP4 servers out there seem not to set the Recent flag
correctly, however, so if SpamPal seems to not filtering some or
all of your mail, try altering this to without
Seen flag, and if it still
doesn't work set it to all. |
|
|
|
::Top:: |
You
can use SpamPal's SMTP auto-whitelisting support to automatically
learn which addresses you send email's to and automatically whitelist
those addresses. The aim of this is to speed up processing of your
email and to keep your friends and contacts emails, from being marked
as spam.
From the main Connections
screen, click Add
to create a new port (or select Properties
to modify the settings)
Select SMTP (specific servername)
as the port type,
and enter in the box below this the name of your SMTP
mail server (this may be listed in your
email program's configuration as outgoing
mail server). |
|
|
|
Make sure that the local port number
setting is 25 |
|
|
Now, go into your email program's configuration
or account properties settings, find the setting for SMTP
server or Outgoing mail server,
and change this to localhost.
Try to send yourself an email message to check that it works.
Now, whenever you send an email to anyone, their
address will be added to the auto-whitelist, so there is no danger
of their reply being tagged as spam.
|
|
Don't
report networking error messages; If
you enable this option, you can suppress any error messages from
SpamPal it may give you, for example, if your system goes offline
or your Internet Provider's server has a problem.
Auto-whitelist receptients of outgoing mail;
Reject messages based on Mail-From;
Reject messages bassed on Client IP;
Add Received Header line to messages; This
options adds an extra Received line to your outgoing message, saying
that your email was sent through SpamPal. Normally this is fine,
however, some ISP's systems
may look at the Received header inserted by SpamPal and refuse
to send the mail message. Turning
off the insertion of the Received header may solve your problem. |
|
|
if you frequently send emails to
yourself, add your own email address to the never
Auto-whitelist list, as
some spammers forge spam mail to look like you sent it yourself. |
|
|
| The options
on the right of the port properties dialog can be ignored, unless
you have SpamPal listening on an IP address other than 127.0.0.1,
in which case you'll need to click the Permissions
button and add this I.P. address to the Local
I.P. addresses list. |
|
|
|
running SpamPal's SMTP support
on an I.P. address other than 127.0.0.1
is very dangerous,
as this could mean your system can be used as an Open Relay |
|
the
RCPT TO address needs to be bounded with < and > in order
for the permissions to work.
For example:
RCPT
TO: someone@domain.com wouldn't work but: RCPT
TO: <someone@domain.com> would |
|
SpamPal
can also be used to filter spam at the SMTP
server level.
Basically, you just have to move your old SMTP relay to another port
or another machine, set up SpamPal where it was, create an SMTP
(specific servername) port in SpamPal's
options dialog, using port 25
(or whatever your old relay was using) and enter the name of the new
location of your real mailserver in the Servername
field.
Tweak the options on the right (the Apply
standard SpamPal filters and plugins
option will only tag spam; the Reject
messages based on client I.P. will reject
email from a DNSBL-listed (or blacklisted) I.P. address).
You'll also need to click the Permissions
dialog and enter all the local email addresses; SpamPal will reject
any RCPT TO: address that is not
one of these. (You can use wildcards
if you want, but be careful!) If this version of SpamPal
will also be used by your own users to proxy outgoing mails, enter
your local I.P. addresses in the
relevent field; the restriction on RCPT
TO: won't apply to connections from these I.P. addresses.
It's probably safest to install SpamPal as an
internal mail relay, with a proper
mail server handling the external connections; however, you lose
the ability to reject mail based on client I.P. address if you do
this. (The standard SpamPal filters should however work fine.)
|
::Top:: |
|
Whitelists are critical
to ensuring that mail from your regular senders and mailing lists
gets through. A whitelist entry is a golden bullet. Regardless of
what any blacklists say, if an address is whitelisted, the mail
will not be marked as spam.
The Whitelist is the inverse of the Blacklist. It has the same format
- one email addresses per line, with '#' meaning the line is a comment
line.
You can also use asterix characters as wildcards, so that you whitelist
anything from an email address (or domain) and it will therefore,
never be tagged as spam by SpamPal. It's useful if you have a friend
at an ISP that's in one of the DNSBL lists - just add them to your
whitelist and their emails won't end up in your spamtrap folder!
For example, you might decide That James Farmer, he's a nice guy,
he'll never send me spam and
add this to your whitelist:
# James Farmer won't
ever send me spam
jjf@spampal.twinlobber.org.uk
Or alternatively you
might think I know lots of people at Hotmail and they never send
me any spam and add:
# Hotmail = nice people!
*@hotmail.com
Entries
in the whitelist will override entries in the blacklist.
This mean that you could (for example) put *@hotmail.com
in your blacklist and then add to your whitelist, the individual
email address of people
you know at Hotmail.
|
|
|
The
whitelist function only looks for email addresses in certain
headers of your email.
These headers are currently: From:,
Reply-To:,
Sender:, Mailing-List:
and Return-Path: |
|
::Top:: |
|
The
normal whitelist is all very well, but you still have to spend time
adding people to it. Wouldn't it be nice if SpamPal did this for
you, well, through the Automatic Whitelist - SpamPal can!
Email addresses get added to the automatic whitelist once they have
sent you email on a certain number of days, so you can rest secure
that people with whom you correspond regularly, will almost never
end up in your spamtrap folder.
It is usually a good idea, to enable the
tickbox Create a log file for
every entry, as this will provide
you with information, as to why the email address get auto-whitelisted.
From the main screen (seen below) you can also, move your auto-whitelisted
emails directly to your whitelist (to keep things tidy), blacklist
them or even remove and never
auto-whitelist them.
|
|
|
| the
auto-whitelist function will only
auto-whitelist emails that haven't
been marked as **SPAM** |
|
Occasionally,
a spammer might forge the email address of someone who is in
your auto-whitelist - for example, a colleague or an alternate
email address or yours. While you don't want to put this person
in your blacklist because they send you lots of genuine email,
you don't want them to end up in your auto-whitelist and bypass
SpamPal's spam-checking features.
To do this, select an email from the list of auto-whitelisted
addresses and then click the remove
and never auto-whitelist button.
The
email address you selected will be removed
and will never
be added to the auto-whitelist. |
|
| If
you are using this, especially in a business, as this is recording
all outgoing addresses, some people might view this as an infringement
upon their privacy, (if you are in UK you need to tell staff
of this policy before you start collecting data) |
|
::Top:: |
Occasionally, a
spammer might forge the email address of someone who is in your auto-whitelist
- for example, a colleague or an alternate email address or yours.
While you don't want to put this person in your blacklist because
they send you lots of genuine email, you don't want them to end up
in your auto-whitelist and bypass SpamPal's spam-checking features.
In this pane you can enter the email addresses of people who should
never be added
to the auto-whitelist.
Just add your colleagues here and you won't have to worry about spammers
forging their addresses to bypass SpamPal's filtering.
You can even add your entire employer's domain - e.g. *@acme-widgets.com |
|
|
::Top:: |
|
SpamPal works by checking
your mail against a number of DNSBL lists which list parts of the
Internet that facilitate spamming. This pane allows you to choose
which DNSBL lists you want to check your mail against.
The right-hand area lists
the available DNSBL lists; those with a tick beside them are the
ones you are currently using. Click on a list, to toggle whether
you are using it or not.
Sometimes one DNSBL list incorporates all the data from another;
in these cases, if the first DNSBL service is selected then the
second will be grayed out in the list.
As the mouse pointer
moves over a list, information about it appears to the right; the
list name, website (click on it to go to that website), and a short
description.
Each list also has a Header Code,
which is used to identify the list in the X-SpamPal:
header, for example: X-SpamPal:
SPCOP
It's usually best to see if changes to your DNSBL choices can find
spam rather than blacklisting individual entries, as Spammers are
continually changing address, so it's not very productive to blacklist
them.
You can copy and past IP addresses here
to see which blacklists would have caught each IP address in the
header. Start with the first Received
line and work your way through the rest of them.
See here for more information on how
to Optimise your DNSBL selection.
|
|
|
Different lists will have different
characteristics. A couple of the more popular DNSBL services will
have been selected by default, but feel free to experiment with other
lists.
If a list seems to aggressive and blocks too much legitimate email (because spam-friendly
providers may well have non-spamming customers too!), you can just deselect it
from the list. You can see which DNSBL marked you email as spam, by looking at
the headers of your email message, see this page
for more details about SpamPal headers. |
During the installation of SpamPal
you are asked what level of filtering you want to use; Safe, Medium or Agressive. You may want to change the setting you originally used
and you can do this by clicking on the
red
arrow (Pre-created Filtering
Strategies) to bring up this screen, where you can default
your DNSBL selection: |
|
|
By using the SpamPal
Status page (right click on the
Systray Umbrella and select Status),
you'll be able to see which of DNSBLs you are using and how effective
they have been during a recent session.
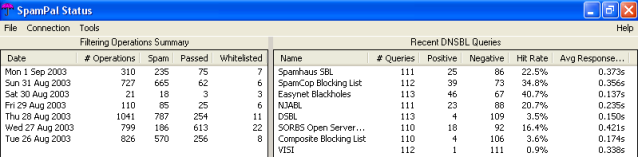
If you look at the statistics on SpamPal's status screen, it will
show you the hit rates being achieved by the various DNSBLs you
are using for recent queries. You will probably notice that some
of the DNSBLs regularly give high numbers, 20-50%,
and others may be very low, or even zero hits.
Deselecting the ones with low hit rates,
will probably improve speed, without affecting your spam detection
capability.
For example, in the screen
below, it looks like Spam-RBL
has caught little spam in this session and therefore, may be a good
idea to deselect this from your list of DNSBLs (public blacklists),
in order to save time.
|
|
|
| In
the left window, note the words filtering operations summary.
This isn't the same as number of messages; if your email
program (Outlook Express is one example) fetches a preview
of your message first and
then the message itself, that's two filtering operations,
so it counts twice. |
|
In
the right window, note the words Recent DNSBL Queries. these
numbers will get reset to zero every time you restart SpamPal,
e.g. when you reboot your machine.
|
|
::Top:: |
If you are receiving a
lot of spam from certain Countries, you can in this pane, select the
Countries which you want to be blocked by SpamPal.
At the time of writing, a lot of spam seems to be routed through
open relays in China. If you are absolutely sure that you
never receive legitimate email from China, you could select this
country in the countries blacklist.
However, you need to exercise great
consideration
when blocking by country, for example, if you're running a global
business, you certainly don't want to be using the blocking
by county feature! |
|
|
::Top:: |
If
you're getting lots of spam with the same email address in the From
line, you can use the Blacklist to have it automatically tagged by
SpamPal.
Basically, the blacklist comprises of a list email address, one per
line, which will mean that all email from one of those addresses will
be tagged as spam.
Blank lines are allowed in the blacklist, and you can add comments
by starting them with a '#', so you can document what you put in your
blacklist, e.g.: #
#Porn spammer keeps emailing me
sexygirl@bigpornspammer.com
sexygirl2@bigpornspammer.com
sexyboy@bigpornspammer.com
# Chain letter pyramid scheme spammer
really_stupid_idiot@aol.com
You can also use an asterix * as
a wildcard, which allows you to stop email with a given ISP in the
From: line.
For example:
# All I get from Hotmail is spam, so let's block it all!
*@hotmail.com
# And I don't know
anyone with sexy in their email
address
*sexy*
You can also use:
*@*.theinsidersedge.com
*theinsidersedge.com
|
It's
generally best not to do this for normal spam, relying on the
DNSBLs or plugins to catch that.
Blacklists are more appropriate for individuals or companies
who are bothering you but aren't generic spammers.
Remember
also that the From:
line in email messages, can easily be forged, so blacklisting
the addresses of all the spams you receive, is largely a waste
of time
Some email programs, such as Outlook have a Junk Mail facility
which will blacklist email address, it's normally a good idea
to disable this feature (which will give you a small speed boost)
and just use SpamPal to do the work. |
|
|
|
::Top:: |
This
is similar to the normal blacklist, except it works on I.P. addresses
and netblocks rather than email addresses.
Like the DNSBL lists, any email from one of the machines on the advanced
blacklist will be tagged as spam. |
|
|
Wildcards
(e.g.. 127.0.0.*) aren't permitted in netblock specifications.
If you want to specify a range, either use the start and end
addresses, e.g.: 127.0.0.0-127.0.0.255
or use the network prefix notation, e.g.: 127.0.0.0/24 |
|
::Top:: |
|
Unfortunately, some aggressive DNSBL's might
place a whole provider on one of it's blacklists.
This is a list of common providers, which if ticked, won't be checked
to see if they are spammers against those DNSBL's
|
|
|
::Top:: |
This
is a list of server IP addresses or ranges which won't be checked
to see if they are spammers. For speed and safety you should add all
of the mail servers of your own ISP, possibly taken from Received
lines of mail you send to yourself,
to this list.
Servers are ignored but just mentioning one of these IP addresses
won't prevent a mail from being marked as spam, if another IP address
in the headers, is that of a spammer. |
|
|
Wildcards
(e.g.. 127.0.0.*) aren't permitted in netblock specifications.
If you want to specify a range, either use the start and end
addresses, e.g.: 127.0.0.0-127.0.0.255
or use the network prefix notation, e.g.: 127.0.0.0/24 |
|
If
you have an email that for some reason, you cannot whitelist
by email address (or by using one of the plugins),
you can add the IP address(s) of the server(s) it uses to the
ignore list, so that it's IP address(s) aren't checked against
the DNSBL's (public blacklists)
Example:
Return-Path: <asasas@mail.cicg.com>
Received: from mail.cicg.com ([216.88.68.110])
by mail3-lx.icom.com (8.12.9/8.12.5) with ESMTP id h6EN50DD032210
for <me@myisp.com>; Mon, 14 Jul 2003 19:05:01 -0400
Message-Id: <200307142305.h6EN50DD032210@mail3-lx.icom.com>
Received: from mail.cicg.com (77.44.d858.cidr.airmail.net [216.88.68.119])
by mail.cicg.com (Post.Office MTA v3.5.3 release 223 ID# 0-58581U100L2S100V35)
with ESMTP id com
for <me@myisp.com>; Mon, 14 Jul 2003 18:06:39 -0500
Content-type: text/plain
Date: Mon, 14 Jul 2003 18:03:55 -0500
From: ADB
Subject: **SPAM** WebRep Alert from AIR-C in MAIN
To: me@myisp.com
X-UIDL: Tc9!!T`'!=*E!>M!
X-SpamPal: SPAM DSBL 216.88.68.110
Add
216.88.68.110 and 216.88.68.119
to the Ignore List,
which will stop this email being checked |
|
::Top:: |
|
This
is an automatic list of server IP
addresses (or ranges) from which you have received email
over several days, which won't
be checked to see if they are spammers,
For
speed and safety the mail servers of your own ISP, possibly taken
from Received lines
of mail you send to yourself, will normally be addess to this list
Even though you ISP's mail servers will end up being placed on the
ignored list, other IP addresses in the headers from a spammer,
won't prevent a mail from being marked as spam
|
|
|
::Top:: |
|
The tagging screen controls
how SpamPal marks mail subject lines and headers. It defaults to
marking the Subject line with **SPAM**
and adding the X-SpamPal: SPAM header
line, after other headers.
You use the Subject line tagging in your email program's message
rules, telling your email program, to move all spam messages to
a special spam trap folder and/or
to delete it automatically for you.
By default, SpamPal will
add two items, to any messages that it thinks might be spam:
The X-SpamPal:
SPAM header;
The string **SPAM**
to the start of the subject line
Using the options in this pane, you can disable the second of these
tags, or change it to some other string of letters, for example:
[SPAM]
Alternatively, you could choose to mark the subject lines with a
duplicate of the X-SpamPal: header,
by ticking the Display X-SpamPal: header
information in subject lines box. This will change the format
of your subject lines will, to be something like this:
Subject: **SPAM**
**SPAM SPCOP 207.218.164.32**
Checking Out!
|
|
|
::Top:: |
| Using
this pane you can modify how SpamPal's User Interface works; for
example you make the status window appear automatically
whilst SpamPal is active (usually while checking your emails) |
|
|
In this screen you can also change
the number of days the filtering statisics (in the main status screen)
are saved for.
You can change which window appears,
when you click on the tray icon with the left mouse button, in this
example (if you have the Bayesian Plugin enabled) you can tell SpamPal
to open the main classification window, when you click on the Umbrella
icon: |
|
::Top:: |
This enables you to create
a log file of what happens while your email program, SpamPal and your
ISP's server all talk to each other, in the process of checking your
mail for spam.
The main aim of this screen, is to help SpamPal Support find any problems
you may be having, while
all the email processing takes place and therefore help fix future
versions of SpamPal. |
|
|
::Top:: |
Every
so often, SpamPal will check back with the SpamPal website to see
if there's a new version of the program available, and to download
an updated list of DNSBL services.
This pane also allows you to control this process, by specifying how
often each check takes place, and whether you'd like a window to open
to inform you when they're happening.
You don't have to check for updates
every day, so the default settings shown here, should be fine for
most people. If you really have to, you can manually check for updates.
The update process is explained in more detail here. |
|
|
::Top:: |
| This
panel enables you to alter various advanced
options (although most users will not need to change anything in this
panel) |
DNSBL
Queries time out after; DNSBL services are sometimes overloaded
with requests, and can be rather slow. To prevent your mail checking
from becoming prohibitively sluggish, SpamPal will time-out (stop
waiting for) DNSBL queries after 20 seconds.
You can use this option to change this interval; lengthen it if you're seeing
the X-SpamPal: PASS TIME-OUT header a lot and
don't mind your email checking taking longer; shorten it if checking your mail
seems to take forever and you don't mind a few extra spams not getting filtered
into your spamtrap folder. |
| Maximum
simultaneous DNSBL queries; allows you to set how many DNSBL
queries SpamPal should make at the same time. If you use lots of
DNSBL lists and/or check lots of mailboxes simultaneously, increasing
this figure can result in a performance increase. |
| Reduce
the number of simultaneous
DNSBL queries to something
low - say, 3 or 4 - and see if this helps with your router
problem. |
|
Don't filter mail at all; allows
you to disable all of SpamPal's spamfiltering features. This options
is also available from the systray
Don't filter mail using auto-whitelist
or auto-ignorelist; disables filtering of mail against the
automatic whitelists. Note that email & I.P. addresses will
still be added to the automatic whitelists, it's just that they
won't have any affect. It effectively turns the automatic whitelists
into lists of seen email and I.P. addresses that are candidates
to be moved to the whitelist after due consideration.
Remember positive (spam) DNSBL results
& Remember negative (non-spam) DNSBL
results; allows you to control for how many days SpamPal
should cache the results of queries to DNSBL services. The higher
each of these are set, the quicker your mail will be fetched, but
at increased risk of SpamPal using out-of-date information and making
more mistakes.
Allow multiple port setting to share a single
port number; This allows you to effectively
have to sets of port configurations using a single port number;
when a connection comes in, SpamPal will use the following criteria
to choose between them:
- If the connection is coming from an I.P. address
that is only on the access control list of one of the port settings,
those settings are used.
- If the connection is coming from 127.0.0.1,
then SpamPal will get the real I.P. address of your machine
and
perform the first test again.
- If SpamPal still can't decide
which port settings to use, it will prompt the user to choose
between them. The user can choose
to have their selection remembered until SpamPal restarts, or
to choose again for each incoming connection to this port.
How could this be useful? Well, let's take the example of SpamPal's
SMTP proxy. Let's say you use two ISPs, example.com and lapmaps.com.
You want to use the SMTP server of whichever ISP you happen to be
dialled into. You could add a setting for both mail.example.com and
smtp.lapmaps.com to the ports list in SpamPal, make both settings
use port 25, and then when you want to send mail SpamPal will prompt
you to choose which you want to use.
Is this a security
risk?
The access control lists determine what I.P. addresses are allowed
to connect to SpamPal. However, as long as SpamPal is configured
to listen on 127.0.0.1 (click on IP Configuration in the Advanced
options pane), only the local machine will be able to connect to
SpamPal regardless of what you put in the access control lists.
So, while SpamPal is listening on 127.0.0.1, this is not a security
risk.
Spampal's
configuration is stored in this folder; This
is the directory:
- where
SpamPal stores it's own configuration files and also of it's plugins.
- that
needs to be backed up, if you are thinking of reinstalling your
operating system.
|
|
|
-
You can also tune the number of connections SpamPal makes;
go to the advanced settings and increase the Maximum Simultaneous
DNSBL queries to 50 (if
you are on broadband/cable/adsl)
- Don't
set the caching times too low
|
|
::Top:: |
SpamPal
is designed as a personal mail filter that will run on same local
machine as your email client. It contains many features that specifically
tailored to this way of working.
However, some people have expressed a wish to run SpamPal as
a service for a local network. Although this isn't advised, it is
now possible.
But before doing it, please consider:
- SpamPal has a GUI, and pops up error boxes in various circumstances.
- The auto-whitelist has privacy implications if SpamPal has
more than one user.
- Tagging mail on retrieval (which SpamPal does) is not the most
efficient way of doing it. A far better solution is to tag mail
when it is received by your mailserver. If you're at the stage
of running SpamPal on a local network, you probably have a mailserver;
investigate the spamfilters that can be installed on it.
If after reading this you still want to be able
to connect to SpamPal from a remote machine, here's what to do.
Go SpamPal's Options pane and
then select the Lan Configuration
pane.
Change the I.P. address setting
from 127.0.0.1 to the I.P. address
of the machine on which SpamPal is running. Now, go to 8.2 (Access
Control) for the next step.
|
|
|
::Top:: |
Following
on from the 8.1 (Lan Configuration) instructions, type the I.P. addresses
of the machines that will be permitted to connect to SpamPal, one
on each line.
You can specify a range of I.P. addresses using either the network
prefix notation (e.g. 127.0.0.1/24)
or by giving the start and end of the range (e.g. 127.0.0.1-127.255.255.255). |
|
|
When
you enter the IP address, be
very careful when you do this - you don't want to accidentally
allow external
machines to connect to SpamPal!!! |
|
::Top:: |
This pane
can be used to a add the filename and location of a text file, which
contains a list of email address
(or IP addresses) to whitelist, blacklist or ignorelist.
The advantage of using this feature over the normal whitelist, is
that it's easy to keep things organised neatly by topic and it also
makes it easy to update them at different times.
You could also place the files on a shared network drive, so you
can easily edit them from a remote pc.
For example:
C:\spampal\friends.txt - could
contain all your friends that you want to whitelist
N:\spampal\work.txt - could contain
your work contacts that you want to whitelist ( Drive N is a networked
drive) |
|
|
::Top:: |
In this pane, you can
add an extra DNSBL service, that isn't currently listed in SpamPal's
normal blacklist/ignorelists pane.
In order to add a new DNSBL, you must first click on the Extra
DNSBL Definitions button (see screen below) |
|
|
Windows notepad should
now open the extra_dnsbl.txt file,
located in your spampal directory. In this file, you will see an example
of what information is needed to enable you to add an extra dnsbl.
For example, the Passive Spam Block List is
a dnsbl; to add this to your public blacklists (dnsbl), cut and paste
the following, onto the end of your extra_dnsbl.txt
file: |
LIST PSBL
NAME Passive Spam Block List
WEBSITE http://psbl.surriel.com/
ZONE psbl.surriel.com
DESCRIPTION An easy-on, easy-off blacklist that doesn't rely on testing
and should reduce false positives
RESULT_CODE 127.0.0.2 # Your server sent spam to trap-server recently |
Save it,
click OK to dismiss the SpamPal
options window then open it again - Passive
Spam Block List should now be listed with the other
blacklists.
However, you will now need to enable this extra Passive
Spam Block List dnsbl by going into SpamPal's
Spam Dection:
Blacklist: Public Blacklist pane, finding the Passive
Spam Block List dnsbl entry and
ticking the enable
box.
Now, when you check your status screen,
you should start to see results from your new Passive
Spam Block List dnsbl. If you want more example dnsbl's
you can add, see the optimize page here |
::Top:: |
|
You can add extra spam-filtering
capabilities to SpamPal by installing Plugins.
Plugins are the second
key to how SpamPal filters out the spam. SpamPal has a powerful
plugin interface and documentation to allow others to add extra
features to SpamPal. Plugins are available for Bayesian filtering,
regular expression filtering, censoring web bugs, logging, spam
quarantining, extra DNSBL blocking functions and more.
You can obtain plugins
from the SpamPal website; install them in the plugins
directory within the SpamPal installation and they will appear on
this pane, but you will have to click on them and then click on
Enable/Disable to enable them
before they will work.
Try the core DNSBL filtering before adding plugins - the DNSBLs
are very effective and may be all you need.
|
|
|
::Top:: |
| Although SpamPal
has a graphical user interface, it does have a few useful command
line options and this section describes how they can be used. |
::Top:: |
|
SpamPal stores its configuration files in the
user profile, or failing that in it's own installation directory.
Advanced users who wish to alter this can do so by specifying an
alternative directory on the command-line, using the -configdir
switch.
For example:
SpamPal.exe -configdir
c:\my_spampal_configdir (If the
specified directory does not exist, it will be created)
This will mean that all SpamPal and Plugin data will now be stored
in the c:\my_spampal_configdir
directory, which has two advantages:
a) It's easy to backup (see here)
b) as this can be a common directory,
it means that more that one user can share the SpamPal settings,
for
example, on a windows XP system, that is using it's multi-user
logon feature. This common directory can
also be placed on a network drive, so that all your network users
can access the same whitelist/blacklist settings etc.
|
::Top:: |
Normally,
you can only run one copy SpamPal at a time. If for some reason you
want to run multiple copies of SpamPal on the same machine (for e.g.,
if you want to listen on two different ports with a different configuration
on each), you should add -allow_multiple_instances
yes,
to the command-line
e.g.:
SpamPal.exe -allow_multiple_instances
yes
If you only want to run
one version of SpamPal, but don't want to see an error message if
you should try to run a second (e.g. if you're starting it from
a batch file that may get run multiple times), you can use the option
-suppress_multiple_instances_warning
yes,
ie:
SpamPal.exe -suppress_multiple_instances_warning
yes
Obviously, combining these
two command-line options would make no sense at all.
|
::Top:: |
|
SpamPal will put a small icon in the system tray
to allow you to access its configuration options.
If you don't often use this icon and you don't want it cluttering
up your tray, use the command-line option -trayicon
none,
e.g.:
SpamPal.exe -trayicon
none
Of course, if you do this then to access SpamPal's
configuration, you will have to:
exit it from the task manager and
restart it, without this option on the command-line.
|
::Top:: |
|